Land Of The Free #1

Summary
- Editorial
- The world of computer underground
- Totally crazy text from BHZ1: description of a Lamer without ever saying the word "Lamer"
- Anonymous mail by telnet
- Text: The Presidents of The United States of America / Lump
- HTML and javascript programming
- How I killed myself with one of my scripts
- Conclusion
Editorial
That's it, I'm there: I'm writing my first ezine on hacking/cracking/phreaking, in short on the Computer Underground. I have long hesitated to do an ezine; indeed I was wondering what I was going to put in it, how to make it not look like a copy of another ezine... In short, at the start I had to put articles on my site and then once my site finished I realized that with the navigation system that I had implemented, adding articles would have screwed up everything.
So I decided to write an emag with the name of my site (www.multimania.com/lotfree) and put it online. Why zipped? Because it compresses several files into one of course!!! Why html? Because it is a format that can be read by all operating systems.
How to make an original ezine? Difficult, of course I'm going to take things that are in all the ezines (like telnet mails) but I don't think I would put anything that I haven't tried myself, at least for practice. A theoretical article, if it is from a reliable source, can be found in this mag. I decided to mix punk with hacking because it's a musical style that I really like. This is already a feature of this ezine. The Land Of The Free will be mainly programming oriented.
I'm making this emag alone (I'm Sirius Black, my nickname for hacking) but that can change. If you want to write an article on hacking, cracking or punk, or even ... anything, write to me at lotfree@multimania.com
I would try to put an mp3 in each mag, not necessarily punk, but artists that I like. On that, enjoy your reading.
SiriusBlack
PS: I didn't put any disclaimer, you know something that says "Warning, this information is for strictly informational purposes only..." indeed you should know that piracy is prohibited... at least if you gets caught. If something is really dangerous (explosives for example) I would put a disclaimer in the article in question. Anyway this first emag is "clean" and needs no warning, but the Land Of The Free won't always be (clean).
"Land Of The Free" is the title of an album by Pennywise, an American Punk-Rock band, I find that this title fits perfectly in the spirit of piracy.
The world of computer underground
We are going to see the basic vocabulary for anyone wishing to enter the dark and swampy world of the computer underground. Indeed the latter is made up of a very specific fauna. Here are the characteristics of the different species that inhabit the world of hacking:
- The Newbie: the newbie is me, it's you, he's a guy who is new to hacking and who is thirsty for knowledge, he can swallow hours of elite words by reading an emag he will have took several days to find... In short, he's a good little guy who wants to achieve his goal.
- The Lamer: he's a guy who doesn't thirst for knowledge, he just wants to show off in front of his friends and pass himself off as a hacker. He spends his time downloading cracks from the internet, mp3s, flooders, nukers and trojans. He uses hacking software but he will never try to find out how it works. It is the privileged target of the elites: indeed what could be more enjoyable than ridiculing a loudmouth?
- The Elites: these are the pros, the big beasts, the guys who hack servers (the stuff with a .com or a .fr at the end ;-) they had contact with computers very early on. Some are real legends (I am thinking especially of Kevin Mitnick and Neuralien), recently I discovered AloneTrio who hacked into a French government server, and who got caught because of his excessive honesty (he warned the server security to fix the flaw, which many white hackers do: help). Unfortunately, we quickly realize that people are very sensitive (how is my server not secure?). Needless to explain why Serge Humpish found himself in prison after revealing that he had found a flaw in the banking service. Anyway, the elites are difficult to cross and they are very discreet so if a guy tells you he hacked microsoft, it's on it's a lamer.
- The Cowboys: he's a guy whose writing is, let's say... slightly painful to read. Example cowboy syntax: 54lut, j3 5u!5 un3 put4!n d3 54l0p3r!3 de C0wb0y5, m0n 3cr!tur3 c'35t tr0p d3 l4 b0mb3. In short, the A's become 4s, the i's !, the S's 5s and the E's 3s. Personally, I can't blame it. V!v€m€nt that!l p455€ 4 the €ur0 !!!
- The Script-kiddies: they are young (15 years old), they are in gangs, they fully exploit known flaws. They are very dangerous because they can cause a lot of damage (the number is their strength). They are not elites but if they continue on their way they will become so.
Then there are the general terms: the hacker is specialized in networks, the Internet; the cracker in programming, software and their protections...; and the phreaker specializes in the telephone network. But the term hacker has encroached on the other two terms: the hacker often designates one of these characters.
It is then necessary to note the good and the bad hackers: the good hacker, he has a PC in front of him, he attacks. The bad hacker, well, he has a PC, he attacks but it's not the same... No kidding, the White Hat Hackers hack for fun, for challenges, they don't destroy or erase anything, that's the case of AloneTrio. Then there is the Black Hat Hacker, he erases, puts viruses everywhere, in short he fucks everything up (synonym: crasher). You should know that the media always rehash the image of the black-hat hacker, which they call "pirates", this term has taken on a derogatory meaning because of them. It is partly because of this that penalties for piracy are so harsh.
A last term to finish? Hacktivism: consists of moving the Underground scene. Hey!! I'm a hacktivist with this emag!!!
Article taken from BHZ (emag)
Absolutely laughed out loud reading this article that I found in a magazine from BHZ (Belgian Hacker Zone), a team of hackers led by Asmodeus. Especially the phrase "YEAH! I'm a hacker, a Telnet delinquent". The image of the hacker who goes to raves and listens to techno is a parody of Neuralien who wrote articles about it in the legendary emag that is NOWAY. Kevin Mitnick is the most famous hacker the earth has ever had. An OS is an operating system... If there's a word you don't understand, send me an email. That says the word Whooper I don't know what it is!! (c:=
2.0 You too can be Mi you fuck
----------------------------------
[**@\/ \/\/@**]
(author: Chu underground!)
I am a hacker, so I install Linux
Well, if you want to be a real hacker asshole, you're going to need Linux.
There, you have 2 solutions: either you're a dirty capitalist bourgeois and you buy it for 150 bucks at Fnac or you're a real asshole, and you download it from the Net Obviously, you're a real asshole so you open your little FTP client and you quietly hit the 20 or 25 hours of download for a Slack or a Debian. Avoid Red Hat, it's too mainstream, you're an uNdERgrOuNd guy now, it's normal, you're a hacker.
Well, you have your Linux, now it's good forget it. No need to break your ass learning a new OS that you will never use because XWing vs Tie Fighter does not run on it. The best solution is to simply fuck lilo, so you're sure you'll only boot under Windows95. It's an elegant solution that many assholes seem to have chosen.
To do this, open a DOS session through Windows and type fdisk /mbr. It will erase lilo which was installed on the MBR of your hard drive, so you won't have to worry about Linux anymore. The main thing is to have it, not to know how to use it.
"Yeah but how can I prove to people that I have Linux and pass for a big rebel?" It's a very natural question.
I thought of you, little loser, and here's a series of sentences to say about Linux, both on IRC and in real life:
- "Linux is too powerful, you're completely free compared to to these OS fascists like Windaube. Anyway, MS is too ripou."
- "Well if you're a beginner, don't go under Linux, this thing is made for eLiTeS, you stay under winfuck."
- "Say, you don't know where I could find libc5.4.36? Because for me 5.4.35 is incompatible with the modifications I made to the kernel."
- "Netscape stinks, it dumps me 10 megas cores as soon as I launch it, I prefer Lynx at least it's not a joke, text mode is better."
- "Ralala the buffoon that it's him! He installed a Red Hat !! Damn it's crap the Red Hats suck only Debian is good, at least you know what what you do you are the master of your system nah really it's ripou Red Hat."
With these kind of small sentences, you will find yourself very quickly classified in the category "OK it's an asshole, but an asshole under Linux", which is the first step to be a real hacker. Now that everyone knows you have your Linux, you have to move on to the next stage, that of the network pro, like the guy who masters ICMP to death.
This is the second stage of your long journey.
I'm just a thirsty for knowledge
Here, you have to put your hand in the wallet. Direction the FNAC, you buy ca$h any books on Unix and on the networks. The main thing is that the title is complicated. A small "rlogin protocol on Ethernet network in sub-addressing" will be of the best effect. Don't hesitate, as soon as you don't even understand the title, you have to buy the book, it's not to read, it's to impress other asshole friends.
A good method consists in buying a book like "TCP/IP volume 43" and taking random words to learn by heart: raw socket, over-addressing, FDDI, telnet for example. Then you put them back in a sentence, even out of context, it doesn't matter, no one is going to check what it means. For example, don't hesitate to post a "Telnet, how many over-addressed raw sockets does it take on an FDDI" on a big fat cowboyz channel, it always impresses, and no one will tell you that it doesn't makes no sense don't worry.
Then arrange these books in your room, with the most complicated titles in the most visible places. Horn a few pages to make it more true. Also take some sheets and draw bogus network diagrams, or put stuff like 123.44.5.34 root/lydia to make it look like you're getting a password like a whiff. You have to play it to death, never hesitate to add more, scan yourself a photo of mitnick and hang it above your bed, or put skull stickers on your toilet to say that now you're a thug, a dangerous guy.
To complete the whole thing and really pass for a hacker, do not hesitate to say bullshit like "I'm just a thirsty for knowledge". OK, you quadruple your second, but it doesn't matter, you still like to learn, it's your great passion and you have a lot of willpower. Make it clear that you never cause damage to the very many machines you enter, say that you are just doing this "for the intellectual challenge". Yes, there, you will have to force yourself not to burst out laughing, but practice in front of your mirror before.
The hacker community has 1 franc
When you're a dangerous guy like you, you have to get together with other bandits to jeopardize state security. months, you will go to a McDonald's in Paris, Place d'Italie, and there you will meet great gentlemen, guys who have rebooted the entire Internet with a Visual Basic program and who have the haircuts of social rebels.
Well, you won't learn much, the losers who come there jerk off to each other saying "Yeah, we're hAcKeRz, we're ruthless, we're really tough, oh damn it's already 6 p.m. I have to go home, my mother will hit me otherwise". You can still have a real thrill imagining that McDonald's is full of cameras and microphones, and that all the employees are DST agents who listen to conversations as dangerous as:
Trouduku1: how much is the Whooper ?
Trouduku2: uh MacDo is doing Whoopers now?
Trouduku1: well yeah they always did right?
The hAcKeRz community also loves raves. It's part of the "rebel no future fuck da society" trip, we swallow ecstasies, we listen to crap music but we don't care, it's great because it's forbidden.
Don't hesitate to go down there, it's undeniably part of the culture of the lost to go and play hot in these evenings.
Damn I'm in the Hack-Hebdo greets!! too foooort!!
You are a real asshole who hacks, and you intend to spread your knowledge to train other losers like you. For that, there are e-zines. We can cite the best known like NoWay or NoRoute where the worst rubs shoulders with the best (and it's a shame for the best...) but also real shit that deserves to be better known, like the excellent Core-Dump which is a veritable farandole of guignolos explaining well-known stuff in French that my cat understands better than me.
Obviously, you haven't read the Unix books, you've never hacked a single machine in your life, so you don't know what to write. Don't worry, you're not the only one in this situation. The best method is to write an article on rap, to tell his last rave or to pump Phrack without understanding anything. Again, if you pump Phrack, don't hesitate to correct the guy outright or add stuff to make it more complicated, no one will check, so go ahead, you're a thirsty for knowledge, don't forget.
YEAH ! I am a hacker, a telnet offender
Now it's clear, you're a real hacker, an IRC scum, an internet thug, you scare all the government agencies and IBM wants to hire you to secure their network because this pedal Henri stuck them with an Internet virus again. It will therefore be necessary, on a daily basis, to behave like a hacker, a real, tough one, that is to say with a hacker spirit and a hacker language. A hacker lives above all on IRC. Once your friends and your family have seen that you have changed, that you are no longer the same man, you will also have to spread the news on IRC and make new friends who will be assholes like you.
No more #poppies or #friendship_fr, now you will have to go to the bottom of the IRC, the cyber-Bronx, nuke-city, where only the real hitters manage to find a place in this universe of violence.
For that, you will have to go from the asshole hacker stage to that of asshole on IRC which is the pete mitnick, namely the c0wb0y.
[**@\/\/\/@**]Copied by Asmodeus[**@\/\/\/@**]09/16/99[**@\/\/\/@**]
Anonymous mail by telnet
What's the point ? It's up to you, we're having a lot of fun with that at my school. What is telnet? Well telnet is a completely legal software that allows you to take control of a PC remotely. Don't get excited so fast!! The computer must be authorized on the network to enter it. What is good with Telnet is that it is a program that is everywhere. You just have to open a console (MS DOS then telnet or start>run>telnet if you are under windows).
Telnet allows you to connect to a computer, but to the port you want. And the port that interests us is the SMTP port, port 25.
So under Linux the command to run will be "telnet www.serveur.com 25" note that www.serveur.com is a bogus name.
Under Windows, Telnet is an application in its own right, you go to terminal>preferences and you check the box echo local to see what you write. Then you do connection> remote system> you enter www.serveur.com in "Host name", you type "25" in port and the rest we don't care. Then you click on "connect".
There the server will present itself: 220 iut.univ-orleans.fr ESMTP Sendmail 8.8.7/jtpda-5.3p ready at Sun, 27 Jan 2002 10:20:46 +0100 (MET)
Then you have to introduce yourself: you put "hello trick", you can leave the word trick, it's not important, he takes it anyway.
He writes to you: 250 iut.univ-orleans.fr Hello Mix-Tours-102-1-123.abo.wanadoo.fr [193.249.65.123], pleased to meet you
You notice that your ip address is put between brackets, it means that a person who knows something about it can know where the email comes from by looking at the headers of the message. Attention on a local network, the name of the post will be in place of the internet address so change post afterwards. But in any case the apparent name will be the one you gave.
You then type: "mail from:satan@enfer.com"
He puts you: 250 satan@enfer.com... Sender ok
Then you type the address of your recipient, note that on a local network, it is often enough to put the login of the guy: "rcpt to:victime@bidule.com"
There he checks the recipient's address, if it's good he puts: 250 victim@bidule.com... Recipient ok
After you type "data", you get: 354 Enter mail, end with "." on a line by itself
In short, you type your text then you end up with a period on a single line (you type enter after of course): 250 KAA09938 Message accepted for delivery
C good c sent ;-)
I'll let you guess what you can do with it: give the chips to a friend, go crazy, sow discord... in short, enjoy yourself.
Please note that the example I took only works locally, I mean that from outside this network you can only send emails inwards. While a person on a local network station can send it wherever he wants.
To find a server that allows you to send emails with sendmail (the software we used for this operation), you just have to do a search on "mail server", you will end up finding a list on a hacking site.
song text
Here is one of the hits of The Presidents Of The United States Of America, they make very crazy rock especially for the lyrics. In short, the word "serious" they don't know, one wonders how they manage to sing such texts without bursting out laughing. It's about a girl, note that Lump means Huge, they paint a portrait of the average obese American, in short they are American and anti-American and super crazy.
Lump
Lump sat alone in a boggy marsh,
totally emotional except for her heart
Mud flowed up into lump's pajamas
she totally confused all the passing pihranas
She's lump, she's lump
She's in my head
She's lump, she's lump, she's lump
She might be dead
Lump lingered last in line for brains
and the one she got was sorta rotten and insane
Small things so sad that birds could land
Is lump fast asleep or rockin' out with the band?
She's lump, she's lump
She's in my head
She's lump, she's lump, she's lump
She might be dead
Lump was limp and lonely and needed a shove
Lump slipped on a kiss and tumbled into love
She spent her twenties between the sheets
Life limped along at sub-sonic speeds
She's lump, she's lump
She's in my head
She's lump, she's lump, she's lump
She might be dead
Is this lump outta my head?
I think so
Is this lump outta my head?
I think so
Is this lump outta my head?
I think so
Is this lump outta my head?
HTML and javascript programming
HTML, you know? This is what allows you to browse the Internet (web pages). JavaScript is a programming language derived from the C language. The common point between the two is that they are languages that do not have to be compiled (unlike Pascal, C, C++...) that is to say that they are not transformed into an executable program. The other common point is that they are intended for the Internet. In addition, Javascript integrates with html.
Here is a very simple html page :
<script language="javascript">
Here you type your program
</script>It is necessary to close the script tag otherwise the navigator will take everything after <script...> for javascript.
The javascript functions that we will use are:
- document.write("your text");
- window.open("the url of the page to open");
- alert("message");
Note that you end a statement with a semicolon, because it's done from C.
The function document.write("hello"); write "hello" on the page, note that in a character string, you must put the <br> tag to go to the line, it is an html tag that does not need to be closed because it is punctual.
The function window.open("page.html"); will open page.html in a new window.
The function alert("hello"); will display a message on the screen, also it is a string so line breaks are possible with "\n" in the string (C language).
Here are some examples :
<script language="javascript">document.write("line1<br>line2");</script>
<script language="javascript">window.open("lotfree1.htm");</script>
<script language="javascript">alert("Virus detected\non this computer");</script>Well, these functions are interesting, but what will they be used for? Well in fact it can be either very funny or very mean.
Let me explain: we are going to apply these scripts to emails, imagine your friend who is in the news, you send him an email with a nice little script that will open a web page for him with beautiful images of beautiful women (blondes of course) very lightly dressed in the process of satisfying the sexual fantasies of males in rute whose level of testosterone is only equivalent to the highest peak of Mount Fujiyama... in short, an image of an orgy!
Imagine, you send him this email while the teacher is just behind him explaining to him for the umpteenth time how we use pointers in C.
Imagine on the head of the teacher but especially the head of your friend!!! (well actually he's not going to find it as funny as you do. Pfff!! No sense of humor!)
The alert message can be a lot of fun if you put some credibility into it. Or just a message: "Guess who's getting hacked? Ok, let's try format c:".
Well, it was all to be nice. Now let out the narcissistic rage sufferer within you.
What interests us is to crash the victim's computer, let's be honest!!!
1 microsoft window that opens is fine, 2 is fine, ... 6 is a pack but 100 is a good chance that it crashes (at least if the victim is equipped with Windows). For this we will see the loops. We will see two of them: the for loop and the while loop.
The for loop:
It is a repetition. The syntax is as follows: for (condition){operation}
The condition is separated into 3 operations: initial condition, stop condition and post-loop operation. Here is an example :
while (true){
alert("My compliments to Windows!!!");
}You guessed it, the person in question will have to click endlessly to close the current window because under win, the N window must be closed for the N+1 window to open... Arf!!! Under linux, they all open one after the other without waiting for anything from the previous one.. but linux does not crash!!!
Here you can do some very cool stuff!!!
By searching a little on the internet you can find other stuff on javascript, once I made a script that displays the powers of 2 with document.write, we hear that the computer has trouble for the calculations at the right some time, sure that above 3 billion that's a lot!!
How I killed myself with one of my scripts
Well yes, I told you that I only put stuff that I had tested!!! I use Windows Me at home, I like my Millenium, it doesn't crash too much (you just need to know how to handle it), but sometimes I put it under test!!!
How? Well, actually running a script in an html page that opens itself twice with a for loop. The 2 new ones each open twice on their own... in short, it's still the power of two!!! The first time I threw it, nothing happened!! The curls froze and I was able to close everything, imagine my disappointment!! I raise it and there it is the horror !!! I had to do several Ctrl+Alt+Del before it closed everything, and then discovered that icons had disappeared!!! Even icons that overlap with those of office documents !!! Worse: I can no longer open the workstation!!!
I try to shut down the PC, it obviously doesn't work. I turn it off with the switch, I turn it back on, scandisc, the invisible icons are back, I can enter the workstation but it's impossible to bring back the icons that have merged with those of office!!! It's nice to delete then recreate the shortcuts (alongside the shortcuts), change their icons... there's always the office document that goes on top!!! Apparently I will always have this problem!!!
You will find the source of this page in flood.txt, it must be renamed to flood.htm to make it dangerous. Here are some screenshots of a result:

flood.txt
<html>
<body>
<script language="javascript">
window.open("flood.htm");
window.open("flood.htm");
</script>
</body>
</html>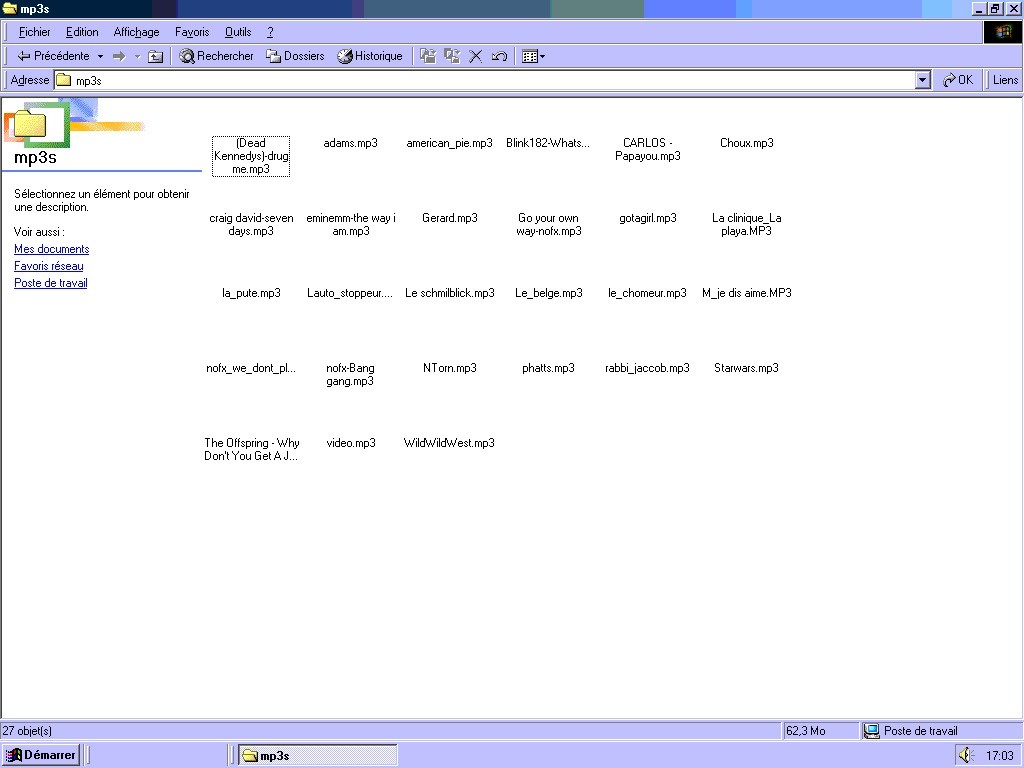
A friend of mine made a nice script: window1 opens window2 then window1 asks to be closed. If you close the 1, the 2 opens the 3 then the 2 asks to be closed and so on... Knowing that this window will have to be closed one day... Here is the script:
<script language="javascript">
window.open("you put the name of the page here");
window.close();
</script>Where the window will wait for window 1 to be closed to open window 2 while the order of the script requires the opposite!!! Indeed all win error messages have the upper hand over other applications and windows waits for you to respond to the request to close the window to continue. It should be known that the process which passes in front of all the others is the program Ctrl+Alt+Delete. Under Linux there is no such expectation so not much happens.
To send these emails: you can go use caramail, hotmail... you type your email in html then you do "send in html".
If the victim has Netscape as an e-mail: you put the html file as an attachment, it opens by itself, practical if it is flood.htm. That said it must depend on the configuration of Netscape. Questions ? ==> lotfree@multimania.com
Conclusion
To conclude I find that there is a lot to read in this page!!! I'm pretty happy with myself, I was able to talk about something that few people talk about (scripts) even if my PC didn't like it. Anyway, this number has everything from the first released ... telnet, bestiary of hacking... I'm going to find what to put in the second release. That's why I would like some help. If you want to write something to put it in the zine you send it to me and if I like it I put it, obviously I respect the copyrights... I have a tutorial on cracking which is nearby so sooner or later he will fall!!
SiriusBlack
To contact me: by email at lotfree@multimania.com or by telephone messaging (I watch it once a week) at 06-78-48-45-65, it's a hacked messaging service so if someone picks up (but apparently there is no one) you hang up, normally a voice tells you: you are on voicemail...
MP3: Bad Religion, a punk rock band that's been touring for 15 years, they founded Epitaph, the biggest punk rock label, they're the ones who discovered The Offspring, they signed NOFX, Rancid (who now have their own label). Here the title is called Supersonic and was released on January 21, 2002 (I'm finishing this magazine on the 27th) it's on the album The Process Of Belief. But I took it from the Punk Rawk Explosion compilation from Punk Rawk N°6 magazine.
It was high quality stereo compressed but at 56 kbps, I don't really know about mp3 compression but I think the compression/quality ratio is great. So good listening!!